Services
IT Security Services
Application Security
We address security-related requirements across each of the three primary domains: application development lifecycle, application development governance and application runtime.
Data Integrity
Data integrity is crucial for business success. Not only data security but clean, meticulous and relevant data is equally important for today’s fast-growing organizations, in order to achieve goals and suppress competition.
Intelligent Survelliance
Protecting your organizational assets, which includes data and physical assets, is the #1 priority for every enterprise. However, the physical threats are often overlooked. Our robust intelligent surveillance solutions enable you to enhance and improve your security control.
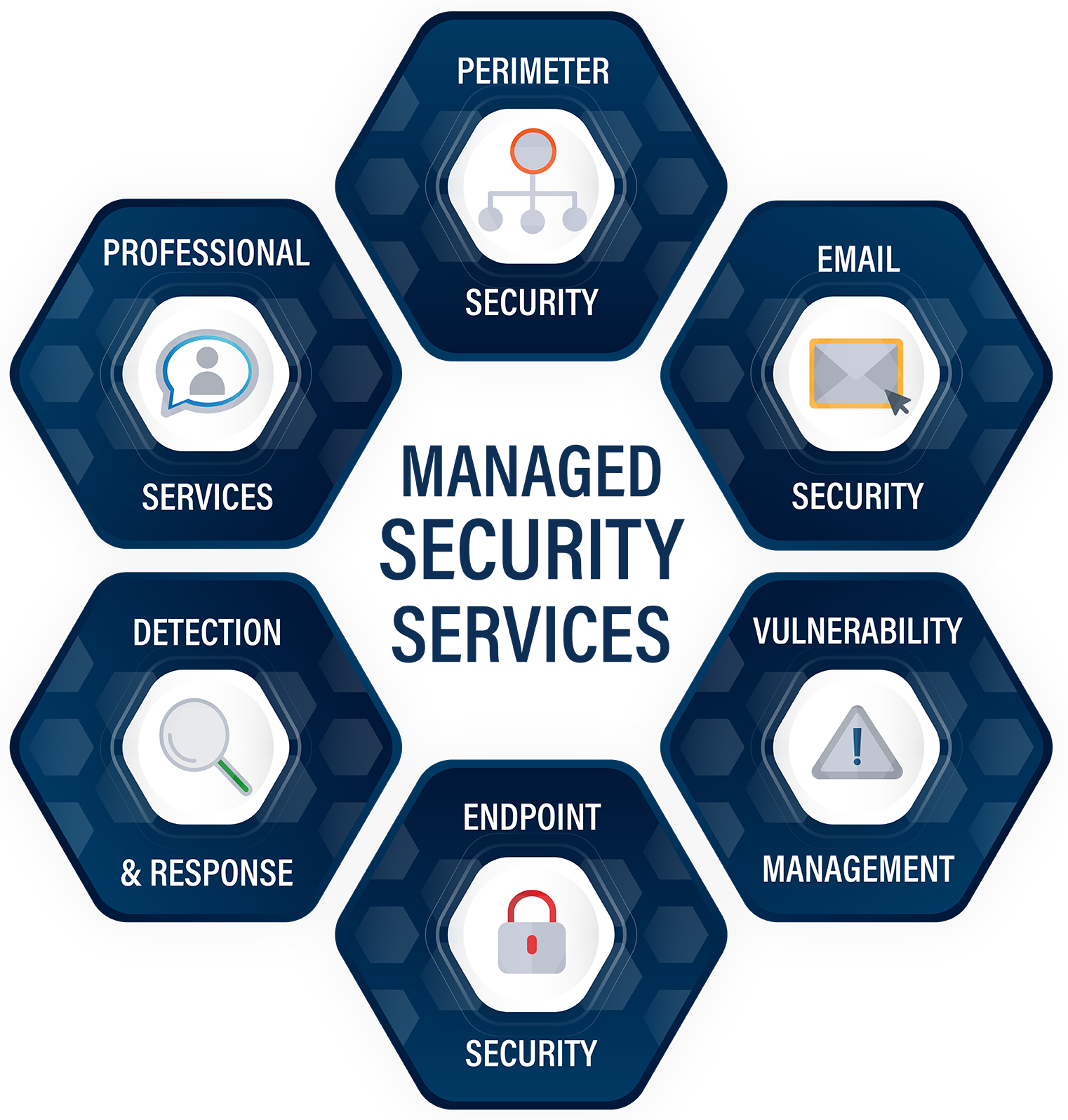
IT Security Services
Protecting Organization’s network perimeter is becoming increasingly difficult and costly, as intruders find new ways to get around your defenses. We can help you stay ahead of evolving threats to your infrastructure while also helping to maximize budget, fulfill support needs and scale based on your network and infrastructure growth and business needs.
We can also reduce cost of defending your infrastructure assets, Enterprise Applications and websites/web portals with efficient OPEX-based pricing models and helps you ensure compliance with PCI, HIPAA, GBLA, FISMA and other regulations.
Ashberry offers a complete range of cybersecurity solutions: from analysis of security issues to development of information security management systems, from cyber security monitoring to the implementation of real-time security intelligence, and support of complex information security systems.
Reasons to choose us
We offer an extensive portfolio of Managed IT infrastructure services that combine flexibility, reliability and responsiveness to deliver tremendous value and efficiency to your business.
Identity & Access Management (IAM)
While your employees need access to information from anywhere, anytime, you need to be confident that your company’s critical data is in the right hands. Identity & access management creates control and visibility into users, and their access privileges.
Infrastructure Security
Businesses today need to secure data at all levels – desktop and network. We design and implement holistic security solutions that are constantly guarding and securing your infrastructure.
Network Security
By combining multiple layers of defenses at the edge and in the network, we help protect your proprietary information from cyber-attacks.
